What is AWS CloudTrail? How to Monitor CloudTrail Logs and Data Events for Real-Time Insights


Try OpenObserve Cloud today for more efficient and performant observability.
Get Started For Free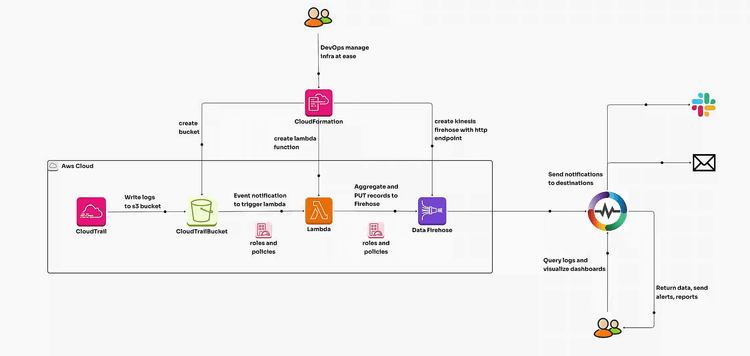
AWS CloudTrail is a vital service for auditing and monitoring your AWS account activity (individual or across all the organizations). It records API calls, data events, user activities, and resource changes, providing visibility into your AWS environment. This ensures compliance, security, and operational efficiency.
Enabling CloudTrail in your AWS environment involves setting up trails to deliver logs to an S3 bucket for storage and further analysis.
Log in to AWS Console: Navigate to the CloudTrail service.
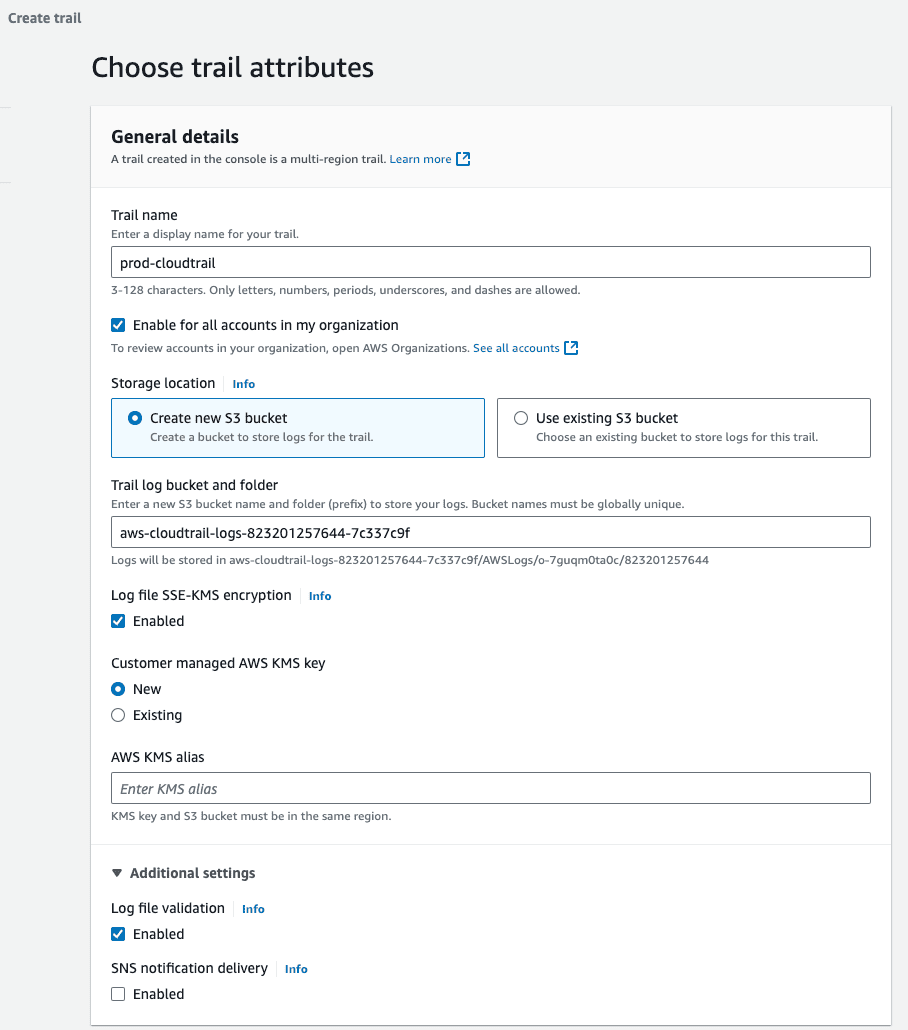
Create a Trail:
S3 Bucket for Storage:
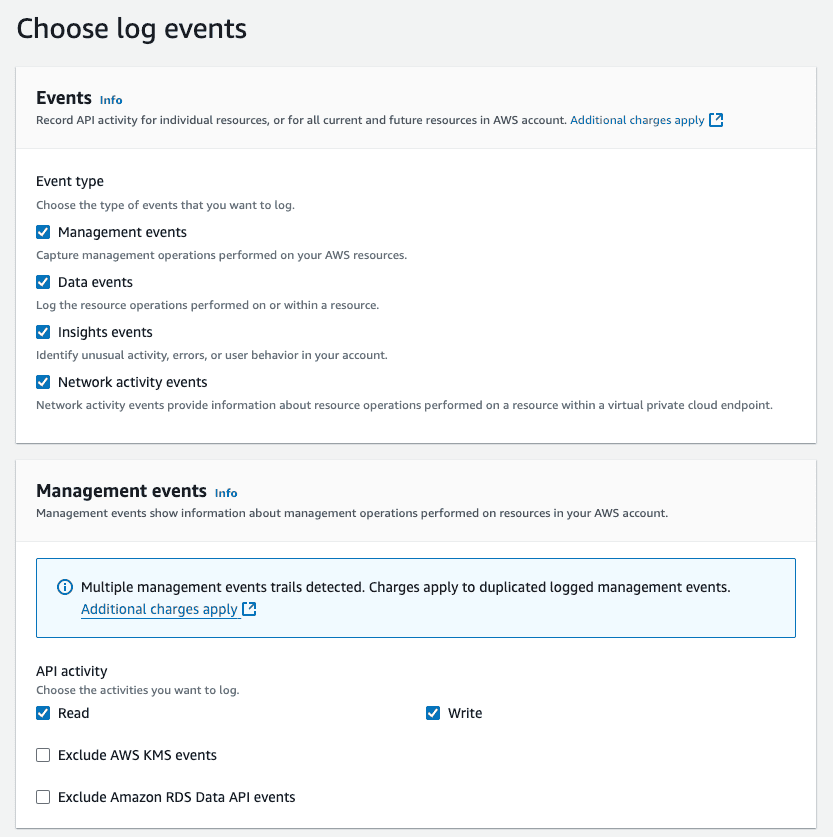
Enable Log Events:
Save and Activate: Once configured, activate the trail.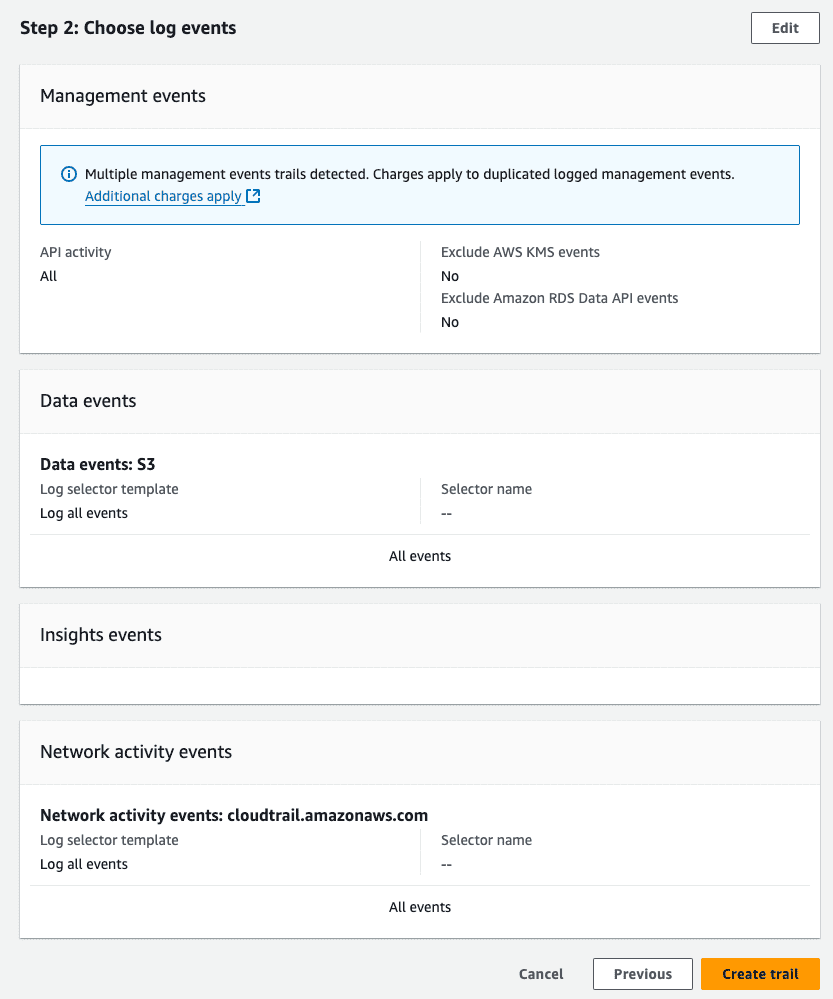
Your logs will now be delivered to the specified S3 bucket, ready for further processing and analysis.
The CloudFormation template automates the setup by creating the following resources:
⚠️ Important Note ⚠️
The provided CloudFormation stack assumes that CloudTrail logs are already enabled in your AWS account. You will need to provide the name of the S3 bucket where CloudTrail logs are stored. Setting up and enabling CloudTrail as part of the CloudFormation stack is outside the scope of this blog.
The stream name in the HTTP endpoint should match aws_orgs_cloudtrail or you will not see data in the dashboard. Alternatively, ypu can also replace aws_orgs_cloudtrail with your custom stream name after downloading the dashboard if you want to use a different stream name
Deploy the Template:
Upload the CloudFormation template to your AWS account.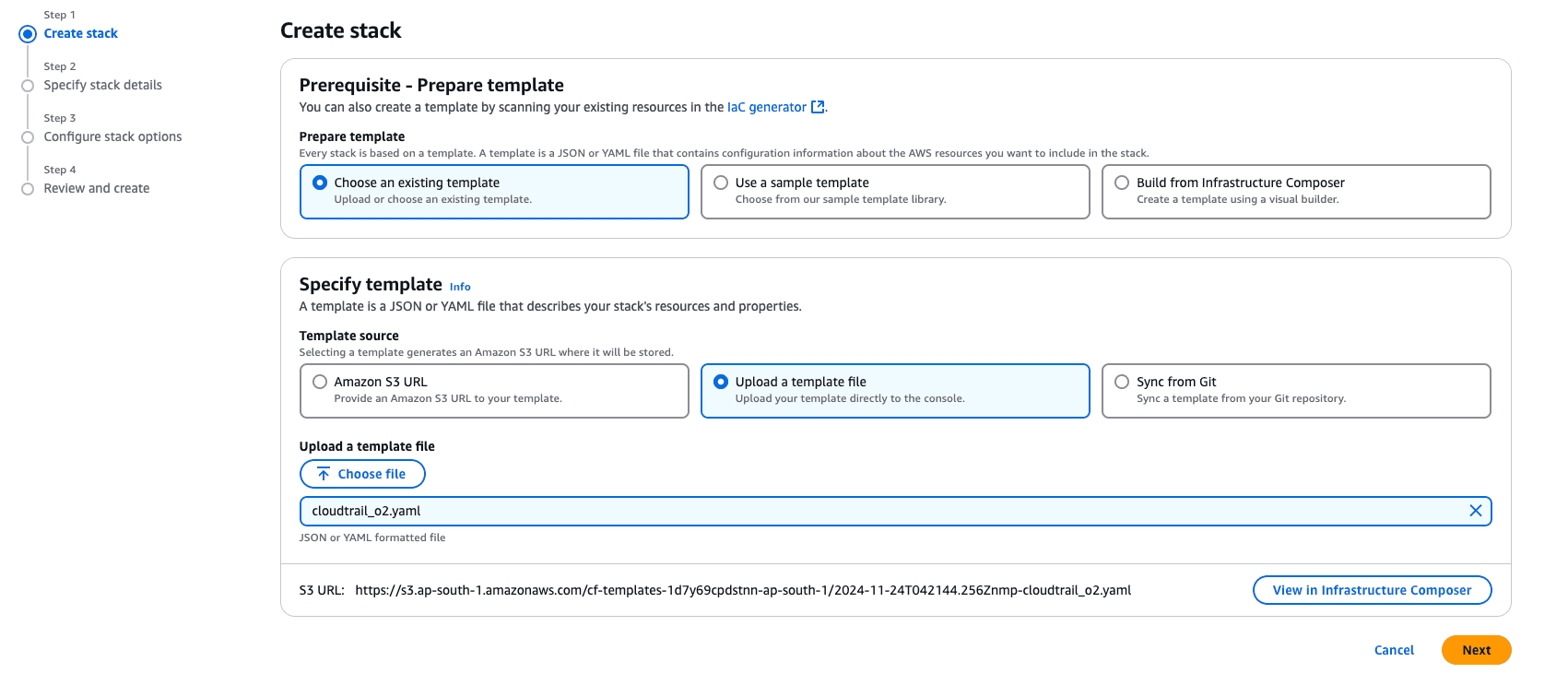
Provide parameters such as:
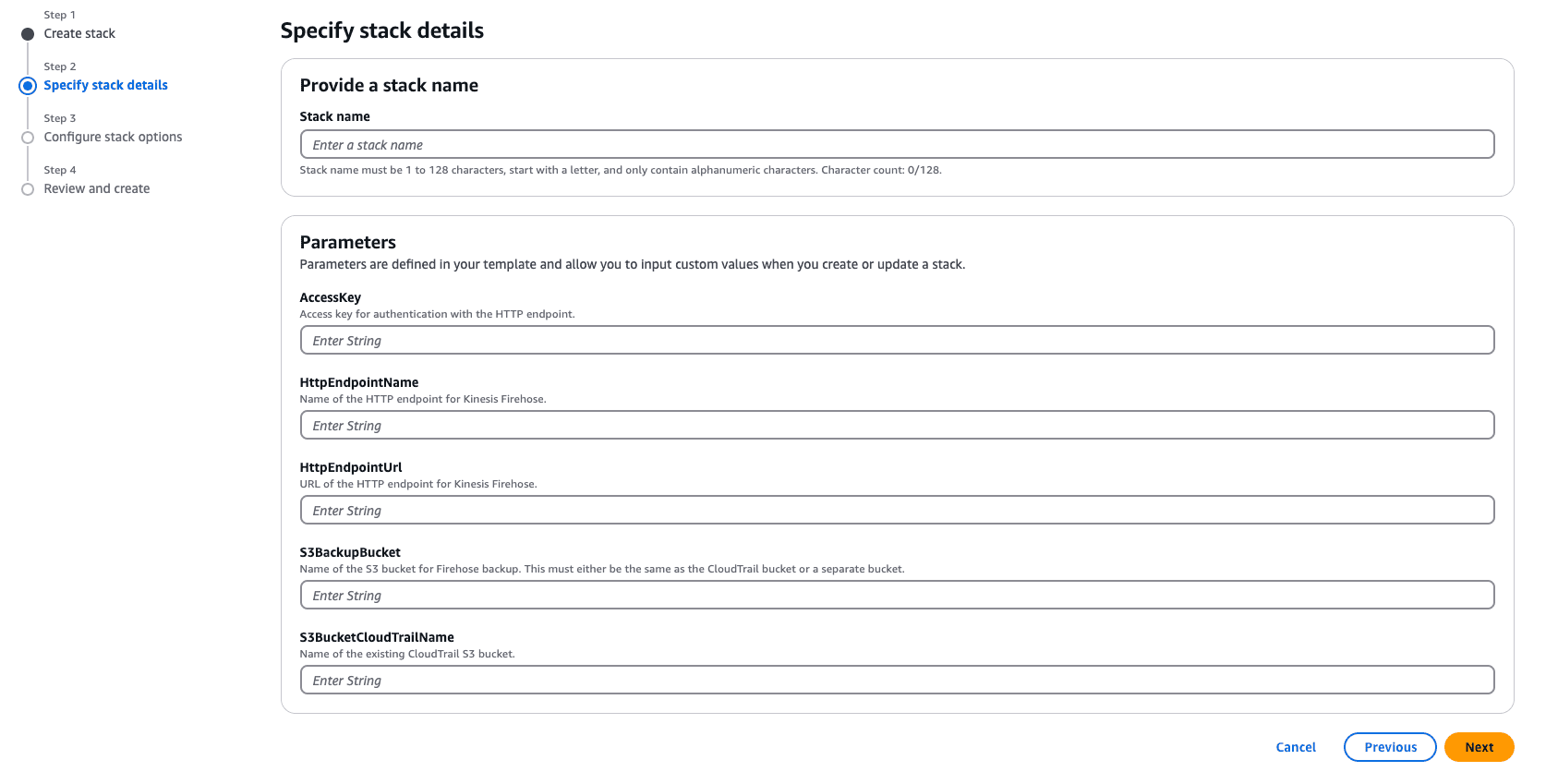
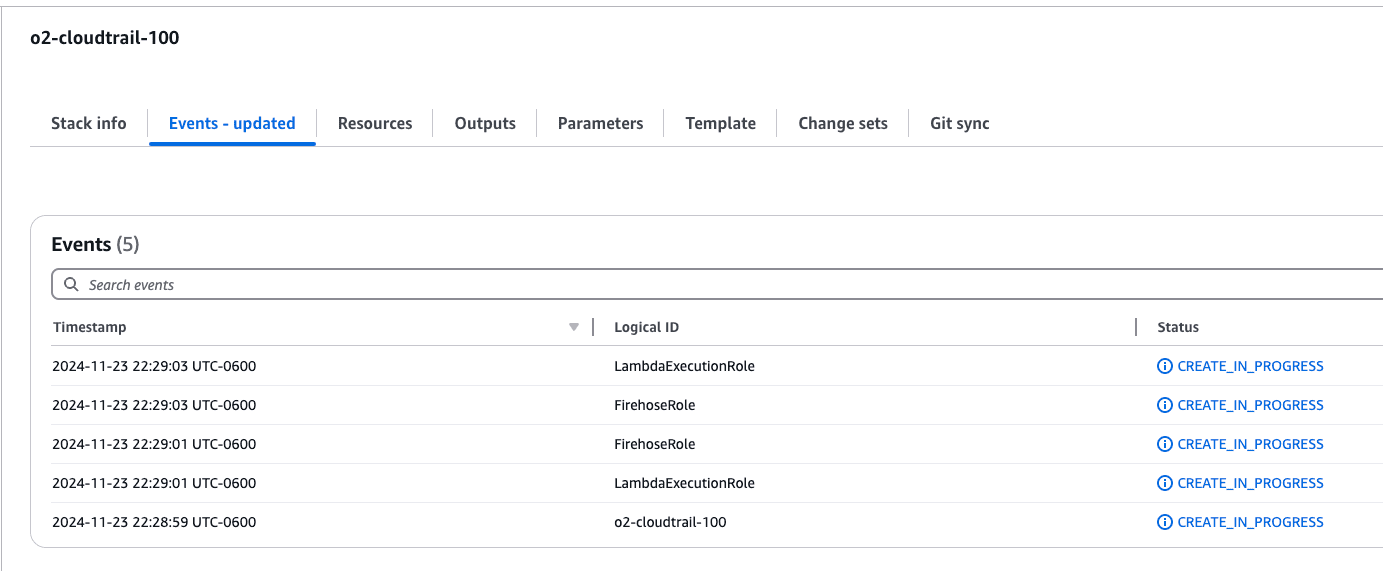
Verify the Deployment:
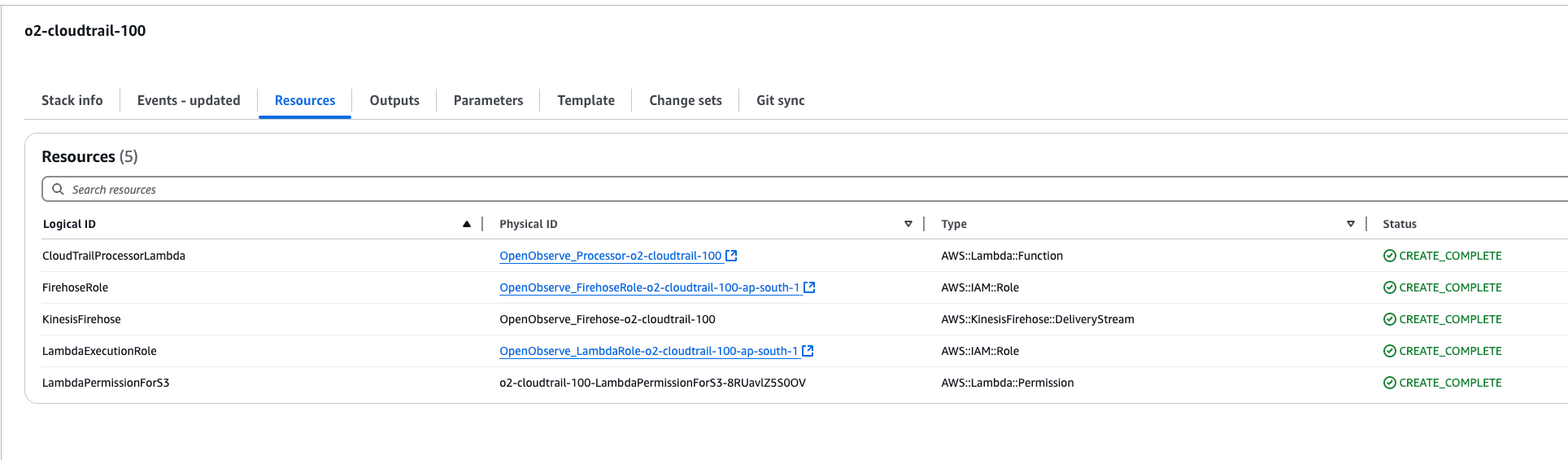
Enable trigger for Lambda:
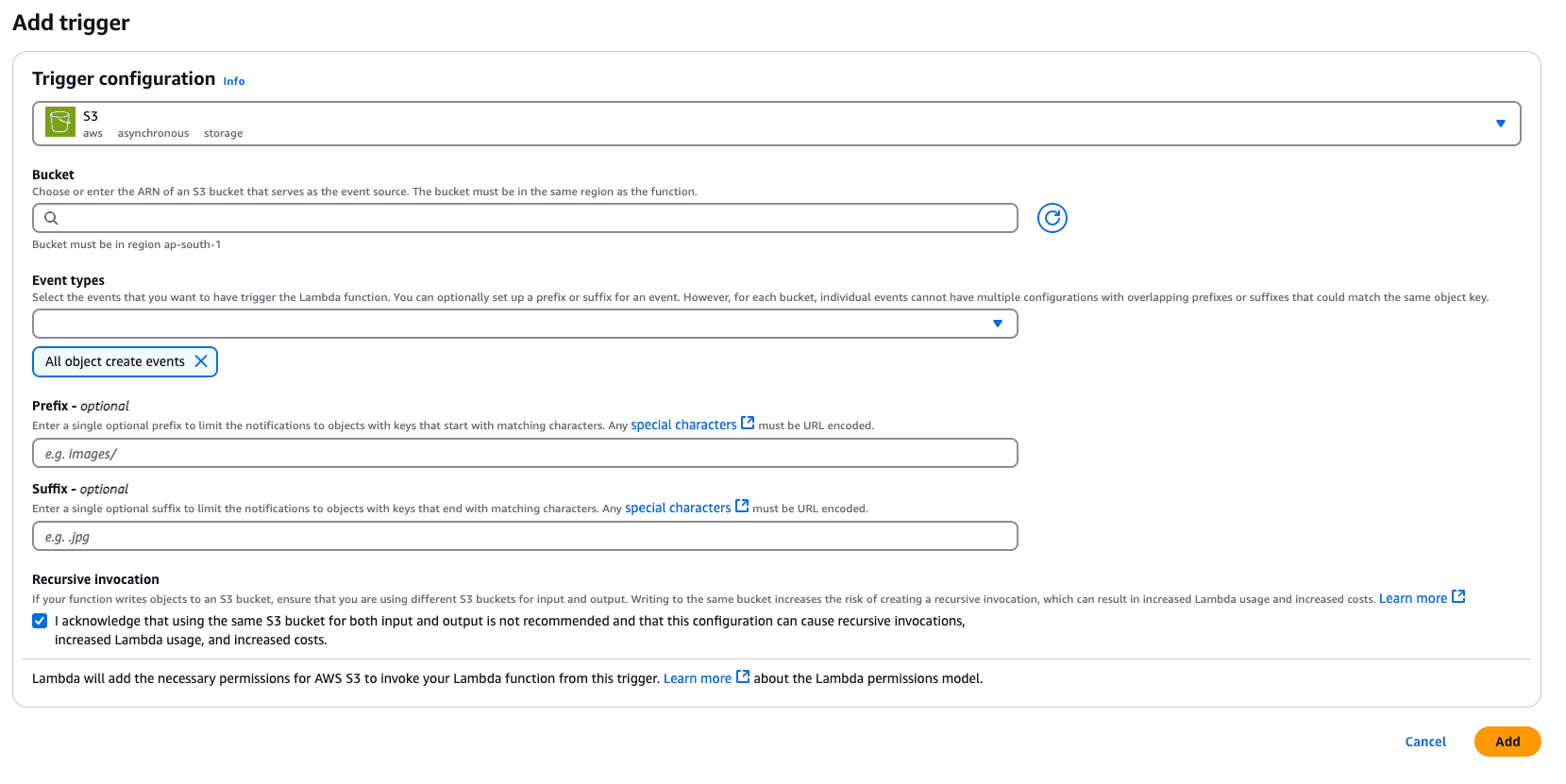
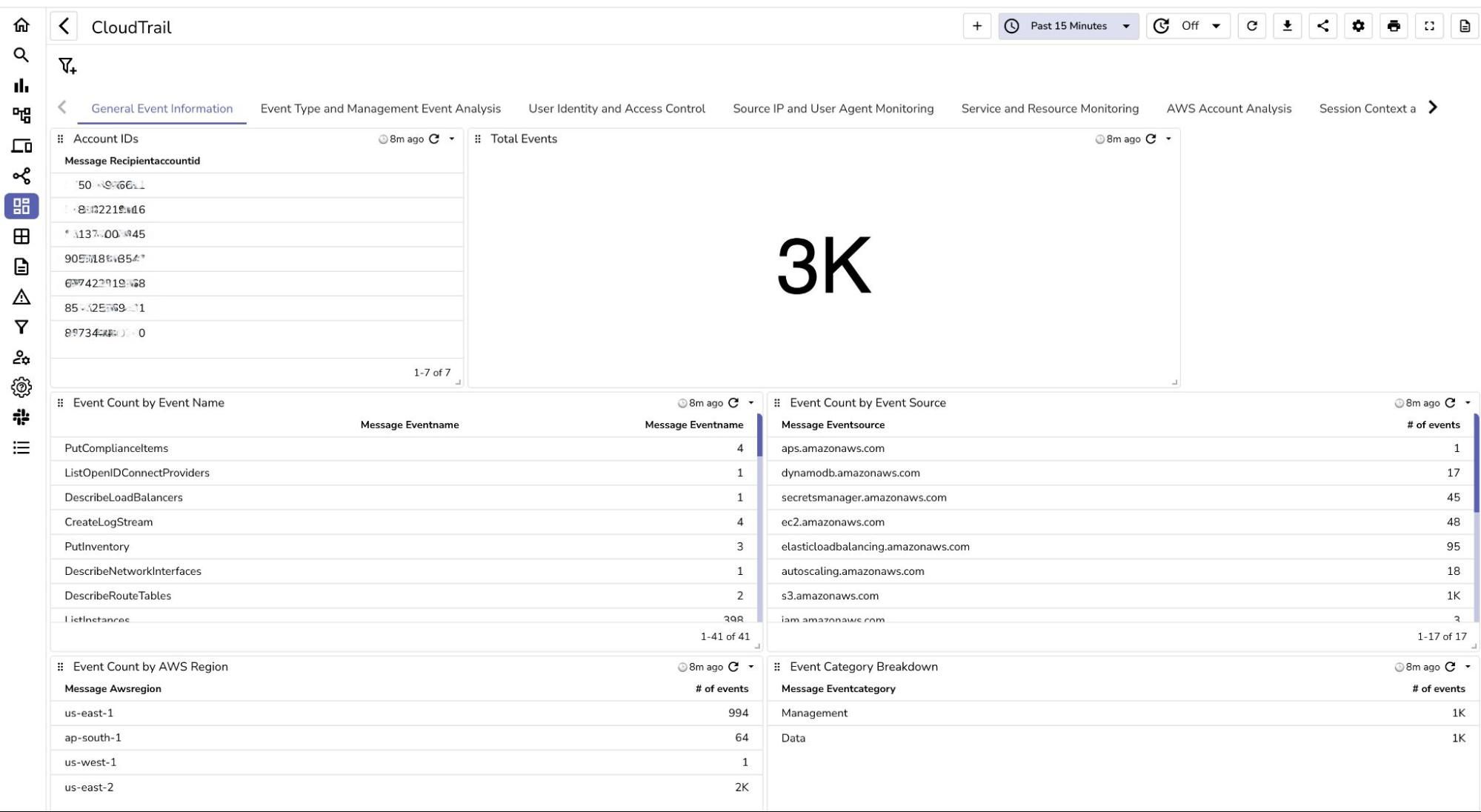
Once the above steps are completed, logs are ingested into OpenObserve, you can visualize and analyze them using dashboards. You can download the dashboards here.
| Feature | Without OpenObserve | With OpenObserve |
|---|---|---|
| Log Storage | Stored in S3 with basic search capabilities | Centralized in OpenObserve with advanced indexing and search |
| Real-Time Monitoring | Not available, relies on manual log analysis | Real-time log ingestion, monitoring, and visualization |
| Search Capabilities | Limited to S3 and CloudTrail console filtering | Full-text search, filtering, and custom queries |
| Data Correlation | Requires manual efforts and external tools | Correlate logs and data events seamlessly in dashboards |
| Alerting and Notifications | Requires custom scripts or additional AWS services | Integrated real-time alerts based on log patterns |
| Visualization and Insights | Requires external visualization tools like QuickSight | Built-in dashboards and panels for actionable insights |
| Scalability | Limited by S3 and manual processing pipelines | Scales efficiently for large volumes of logs |
| Security Incident Response | Slower due to manual log retrieval and analysis | Faster with real-time alerts and context-rich dashboards |
 AWS CloudTrail is indispensable for monitoring and securing your AWS environment. By leveraging a CloudFormation template, you can automate the setup of an efficient log pipeline to OpenObserve. This not only saves time but also provides a powerful way to analyze and visualize your AWS activities. With detailed dashboards and log analysis, you can ensure compliance, detect anomalies, and optimize your cloud operations. Get started with OpenObserve and gain control of your AWS cloudtrail logs.
AWS CloudTrail is indispensable for monitoring and securing your AWS environment. By leveraging a CloudFormation template, you can automate the setup of an efficient log pipeline to OpenObserve. This not only saves time but also provides a powerful way to analyze and visualize your AWS activities. With detailed dashboards and log analysis, you can ensure compliance, detect anomalies, and optimize your cloud operations. Get started with OpenObserve and gain control of your AWS cloudtrail logs.

Chaitanya Sistla is a Principal Solutions Architect with 17X certifications across Cloud, Data, DevOps, and Cybersecurity. Leveraging extensive startup experience and a focus on MLOps, Chaitanya excels at designing scalable, innovative solutions that drive operational excellence and business transformation.