Log Ingestion Basics
Introduction to Log Ingestion
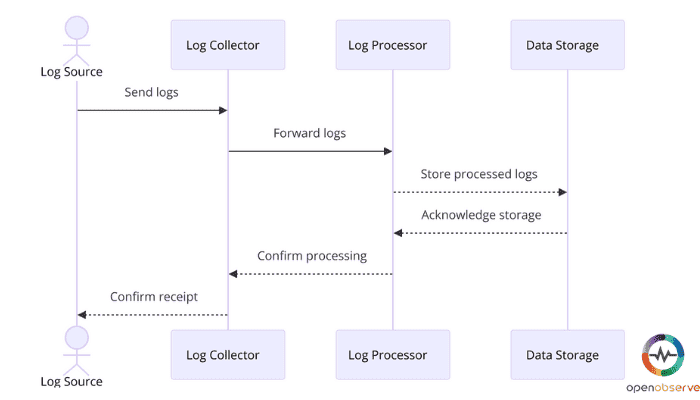
Suppose you were trying to watch and manage everything going on in a city, like how the traffic moves, people’s locations, power usage, and public safety; you’d probably get a headache. There’s just so much to keep track of! In IT and cybersecurity, you’re often dealing with large volumes of data from various systems and applications, which can be overwhelming, too. That’s where log ingestion comes into play. It helps you streamline all that data (or logs) by collecting, processing, and storing it in one place so you can monitor your IT resources, improve security, and maintain compliance.
Now, to get you started on the basics, let’s explore log ingestion, its importance, how it works, best practices, and more to help you understand this important task.
Why Manage Your Log Ingestion
Why do you want to manage it? Well, for starters, it prevents you from collecting and storing more data than needed. Here are some more reasons to manage it:
Cost Implications
Log analysis and SIEM tools are often priced per volume. The more logs for analysis, the higher the cost. Effective log management can help cut down on unnecessary costs and optimize tool usage.
Alert Fatigue
A rash of log ingestion results in a deluge of alerts. It becomes difficult to distinguish which alert needs immediate attention and which can be disregarded. This condition, known as alert fatigue, can result in IT staff becoming desensitized, leading to longer mean time to detect (MTTD) real threats.
System Overload
One of the most significant issues with log management is the SIEM system being overloaded with logs, which it needs to analyze. If your SIEM receives and stores excessive logs over time, it may process them less efficiently, potentially causing slower performance. Effective log management ensures that your SIEM tools work smoothly without being bogged down by irrelevant data.
Now that we understand why managing log ingestion is important, Here are some different types of logs that should be prioritized for seamless monitoring and security.
Key Types of Logs for Ingestion
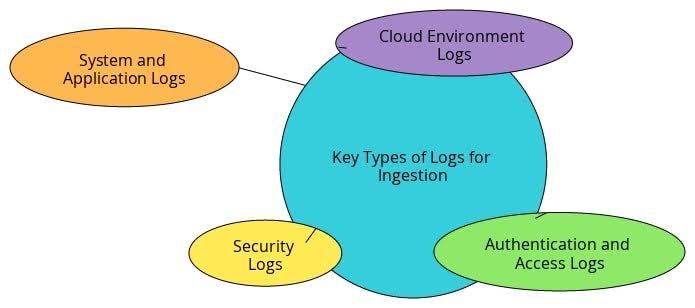
Security Logs
Security logs enable monitoring, detection, and response.
- Firewalls: Log permitted and denied traffic.
- Network Devices: Monitor data flow and network irregularities.
- IDS/IPS: Log intrusion attempts.
- Antivirus: Log malware detection and cleaning.
Authentication and Access Logs
Authentication and access logs help confirm and review user access.
- Active Directory (AD): Log on to users and group policy modifications.
- VPN: Log remote access connections.
- Multi-Factor Authentication (MFA): Log authentication attempts and successes.
System and Application Logs
System and application logs allow for continued smooth running and rapid resolution.
- Operating Systems (OS): Log system errors, user interactions, and resource consumption.
- Databases: Log query performance, errors, and activity.
- Web Servers: Log HTTP requests, errors, and access.
- Critical Applications: User interactions and application-specific events.
Cloud Environment Logs
Cloud logs help to understand the cloud environment and services.
- Cloud Access Logs: Record who accessed what resource and when.
- Infrastructure Logs: Record when changes are made to the cloud infrastructure components.
- Service Activity Logs: Record events related to the use and performance of cloud services.
However, not all logs are created equal. Let’s check out how to identify and handle low-value logs next.
Identifying Low-Value Logs
Along with the retention and normalization of logs, another effective log management practice is to exclude low-value logs to improve the efficiency of log analysis for security and monitoring purposes.
Common examples of low-value logs
- Printer logs: In most cases, print events are not of security value.
- Debug logs: Volume is high, critical information is low. Debug logs are primarily of use to developers when troubleshooting issues.
- System notifications: Maintenance messages from systems that do not provide security value.
- Environmental logs: Sensor data such as temperature, humidity, etc. that are not cyber security related.
Log Ingestion Practices
Sending Data to Log Management Systems
To configure log forwarding:
- Syslog: Standard protocol to send device logs to a log server.
- API Integration: APIs to post logs from apps to log management systems.
Log Input Options
You can gather logs from multiple sources:
- Agents: Software that’s installed on hosts to gather and send logs.
- Log Forwarders: Relay servers that group send logs to a log server.
- Direct Integration: SaaS apps & services with native log forwarding.
Using LogSource and Configuration Templates
- LogSource: Standardized config template for specific datasets to ensure logs are properly ingested.
- Configuration Templates: Standardized templates that can simplify configuration and management.
Deviceless Logs and Their Management
Logs from cloud-based services may not always be automatically integrated into traditional log management systems and require special handling and integrations.
Log Filtering Recommendations
It is important to filter private information from your logs for privacy and regulatory reasons. Some methods include:
- Masking: Hiding data that is sensitive
- Anonymizing: Removing personally identifiable information (PII).
- Redaction: Removing logs with private data altogether.
Great, now that you’re familiar with the log ingestion practices, let’s talk about some best practices to keep everything running smoothly.
Best Practices for Log Ingestion
Log Prioritization and Filtering
To avoid struggling through every log event, focus on the logs that matter to you by:
- Prioritizing log sources: Determine which systems and apps are critical to your business.
- Applying filters: Discard logs that have lower value, so that you can lessen noise.
Regular Review and Fine - Tuning
Regularly review the log collection setup and make changes as needed:
- Delete unused log sources: If a system is decommissioned, its log sources shouldn’t still be collecting logs.
- Update filters: Filtering rules should be adjusted as requirements change.
Effective Monitoring and Alert Management
To avoid alert overload and guide the response priority:
- Use thresholds: A threshold can trigger an alert when a certain threshold is met, ensuring only important events create alerts.
- Correlation: Correlation rules can establish patterns and help tie together events from various sources that may indicate a problem.
Conclusion
Log ingestion can seem daunting, but it is an essential step to maintaining a secure and healthy IT environment. Understanding log types, the need for effective log management, and adhering to some recommended best practices will help ensure that your log data remains a valuable asset and not a massive headache. It’s not just about collecting data; it’s about collecting the right data and knowing what to do with it. So, prioritize your logs, eliminate the noise, and keep your systems in check.
You can analyze your log data with OpenObserve. Have a look at OpenObserve now and get a grip on your IT process!



