What is JumpCloud and How JumpCloud Directory Insights Help Customize Security Reports for Advanced Monitoring


Try OpenObserve Cloud today for more efficient and performant observability.
Get Started For Free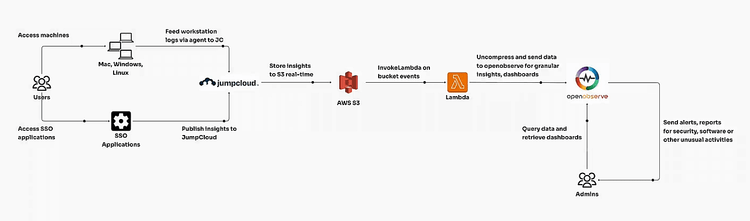
JumpCloud provides a centralized platform for managing identities, devices, and access, crucial for organizations with distributed teams or remote workforces. A key feature, JumpCloud Insights, offers actionable data on user and system activities, essential for security monitoring and compliance. In this guide, we’ll cover forwarding JumpCloud Insights to AWS S3, using a Lambda function to ingest these logs directly into OpenObserve, and setting up visual dashboards for comprehensive security observability.
First, set up AWS S3 as the destination for JumpCloud logs by following the instructions in the JumpCloud AWS Serverless App Directory for Insights. This process enables JumpCloud Insights data to be forwarded to an S3 bucket, acting as a raw data storage location before processing.
You can choose the ingestion time as needed. I opted for every minute since I prefer near-realtime.
With this setup, JumpCloud will start sending data to your S3 bucket as logs are generated, allowing access to raw security and operational data from JumpCloud Insights.
To streamline log ingestion from S3 to OpenObserve, set up an AWS Lambda function that automatically transfers new log files into OpenObserve as they arrive in the S3 bucket.
Download the src.zip from github that will be used in the next step.
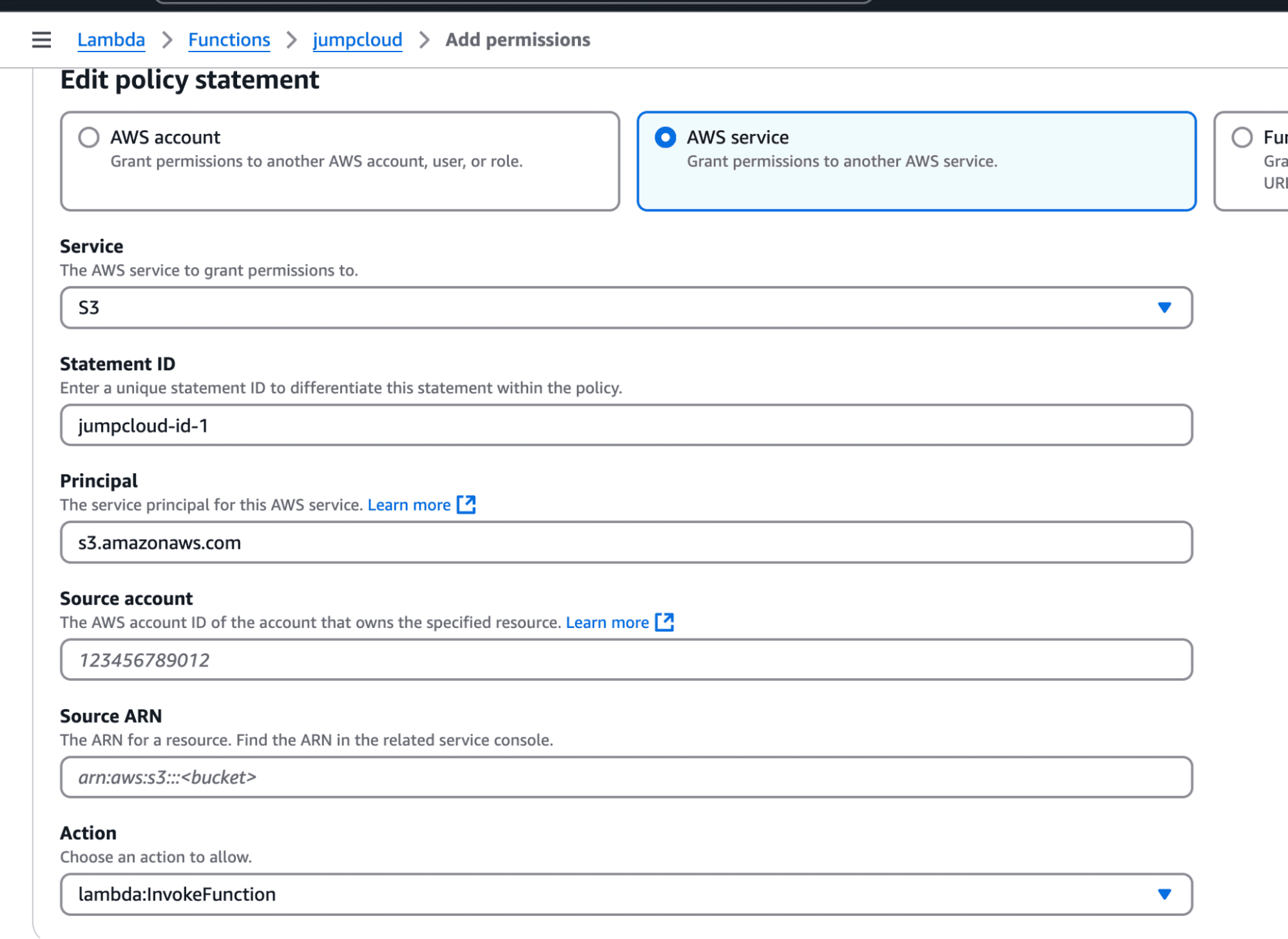
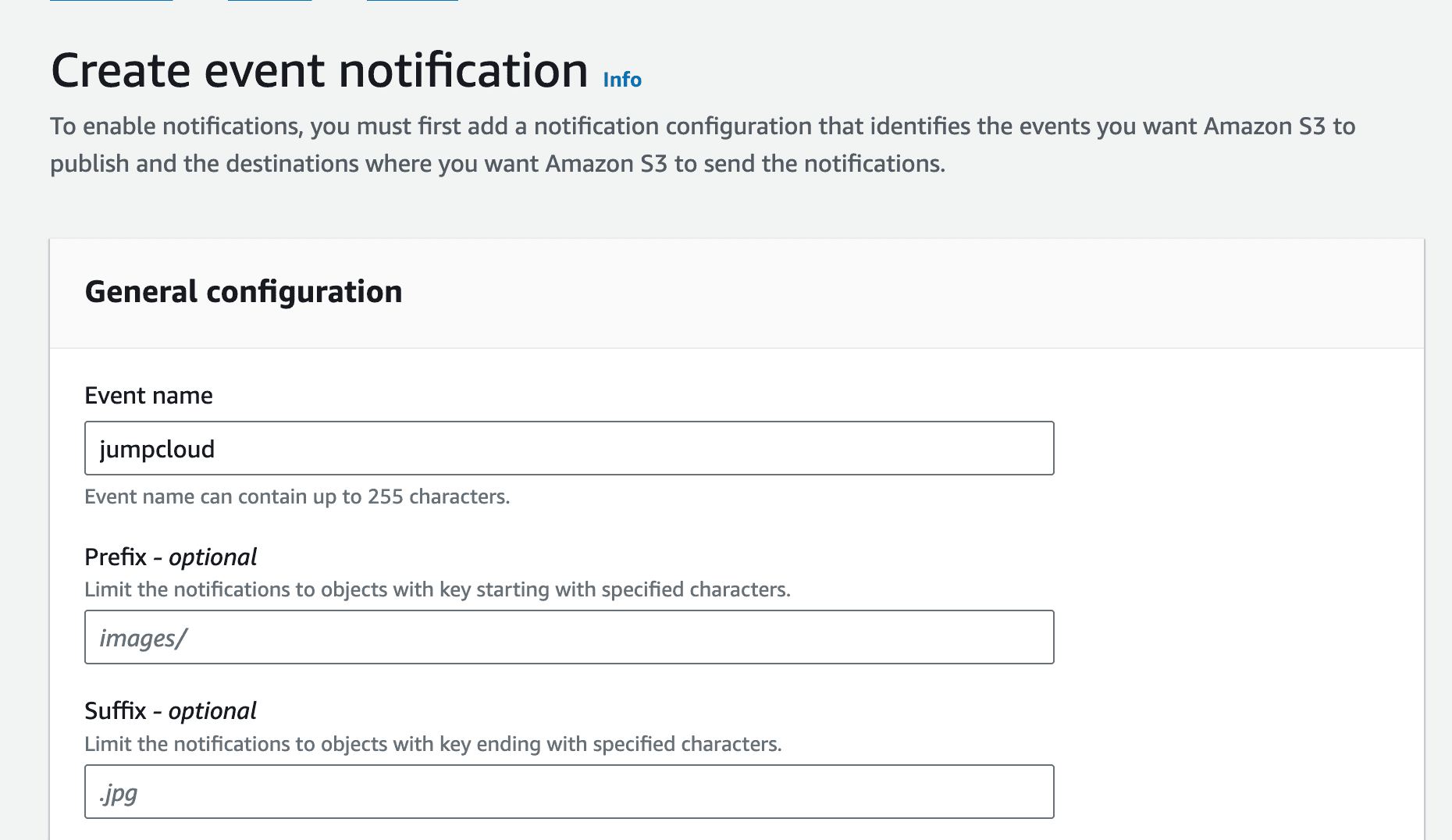
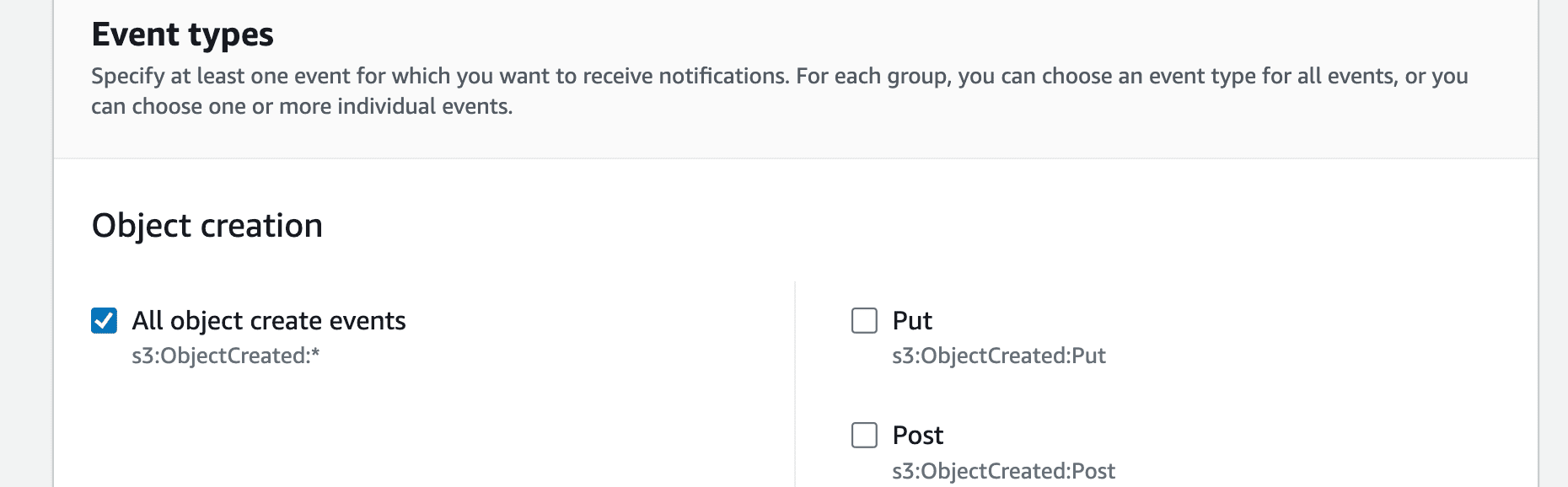
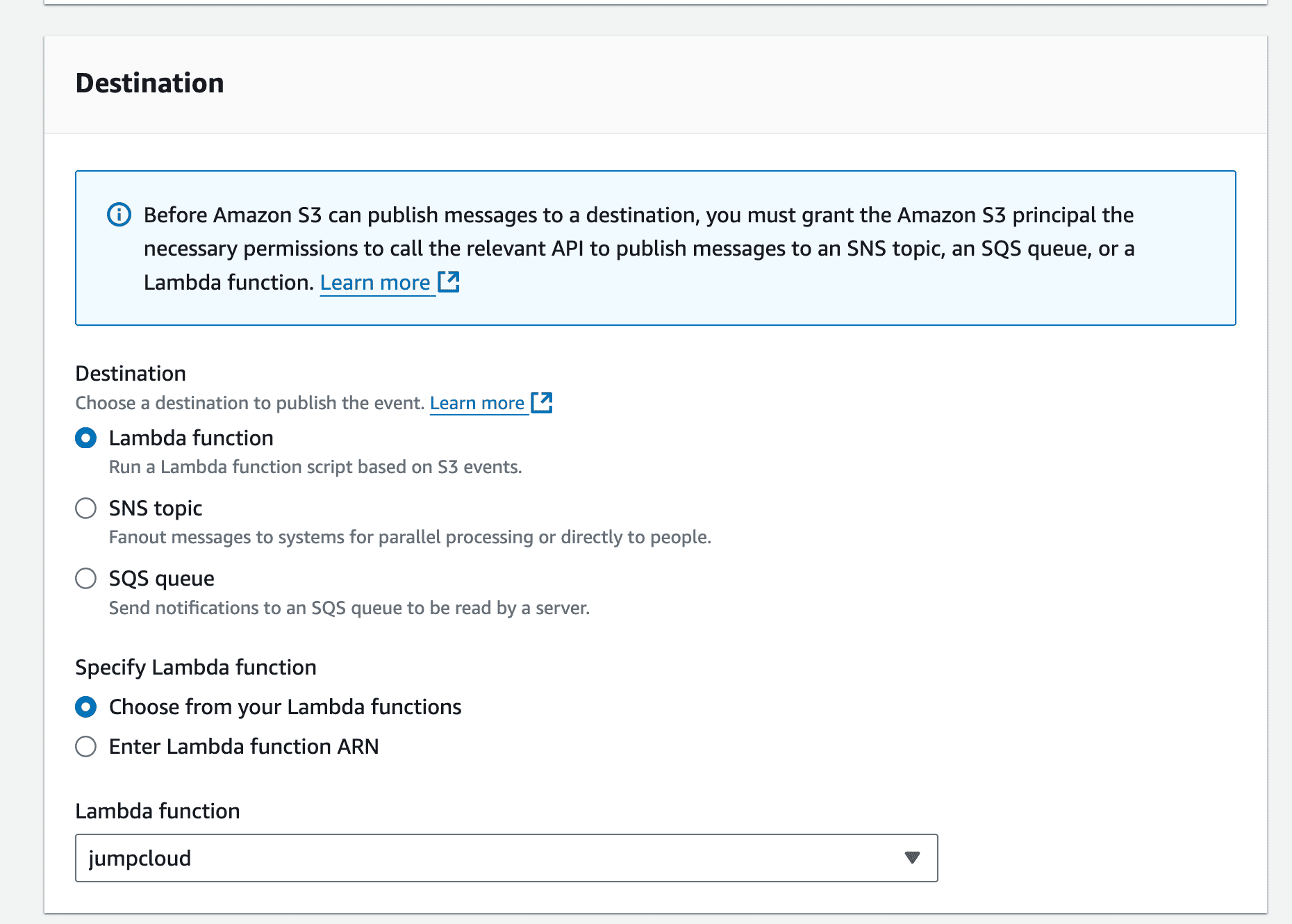
This will now start sending the events to OpenObserve when there is any event in the bucket.
You can simply upload the JumpCloud dashboard that was designed by the OpenObserve team to get started quickly on security and other insights.
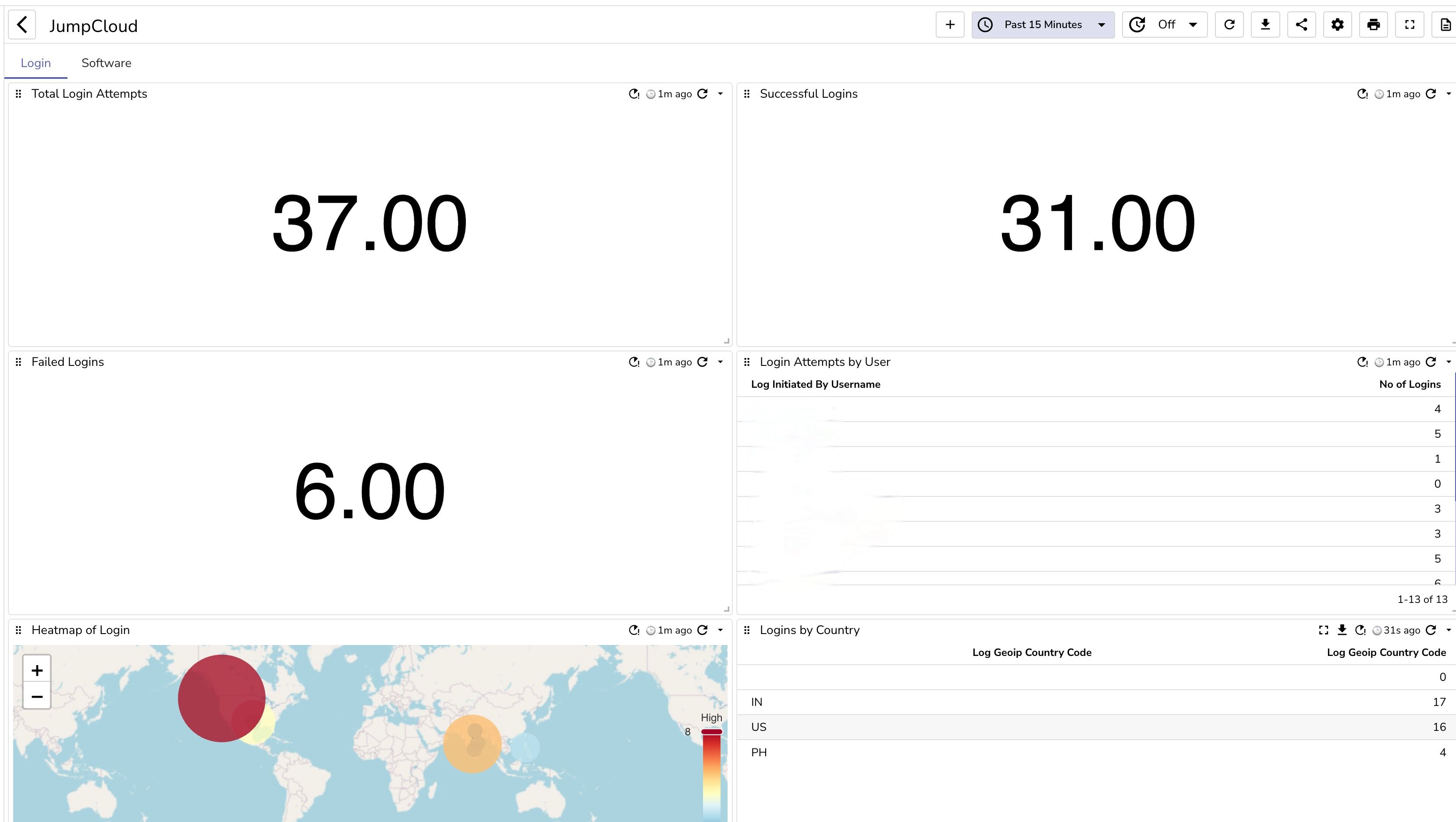
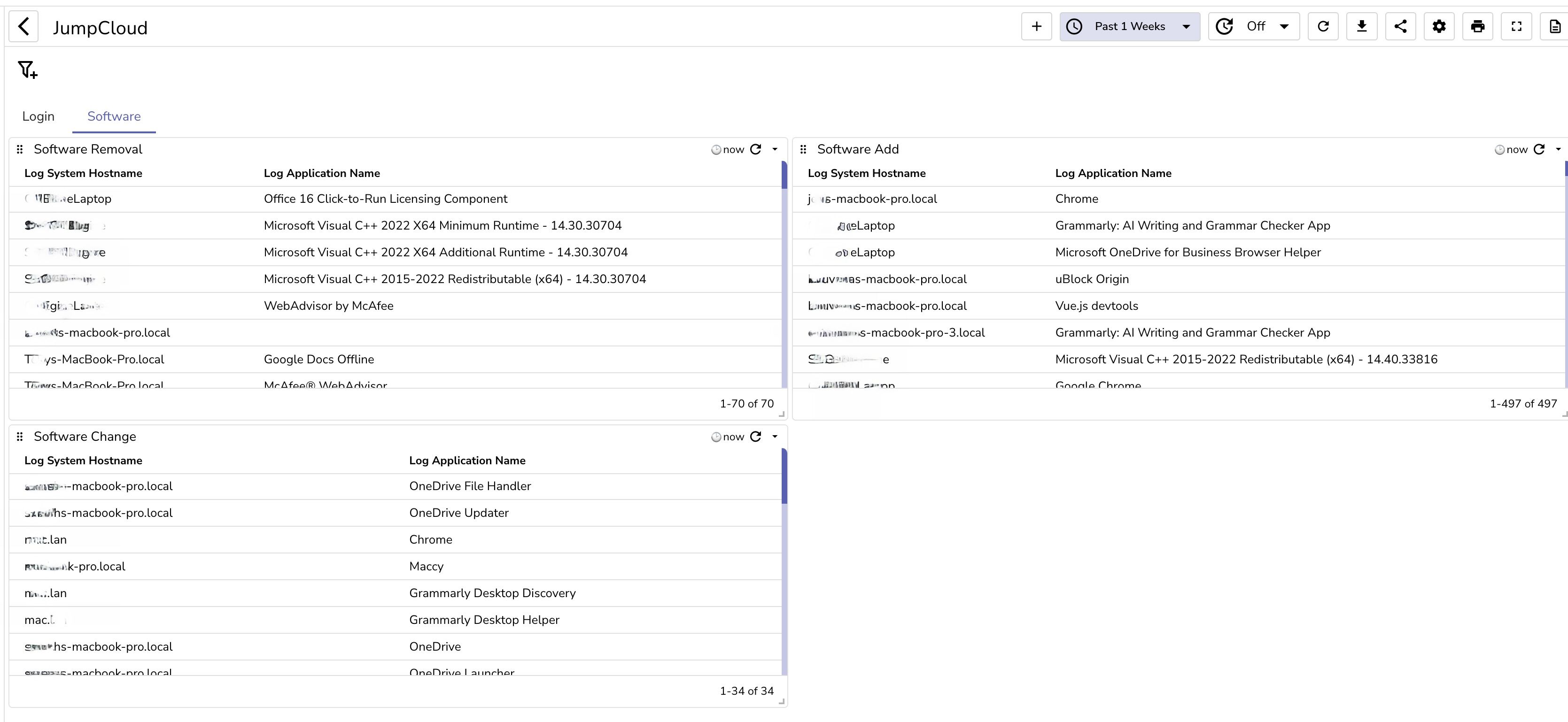
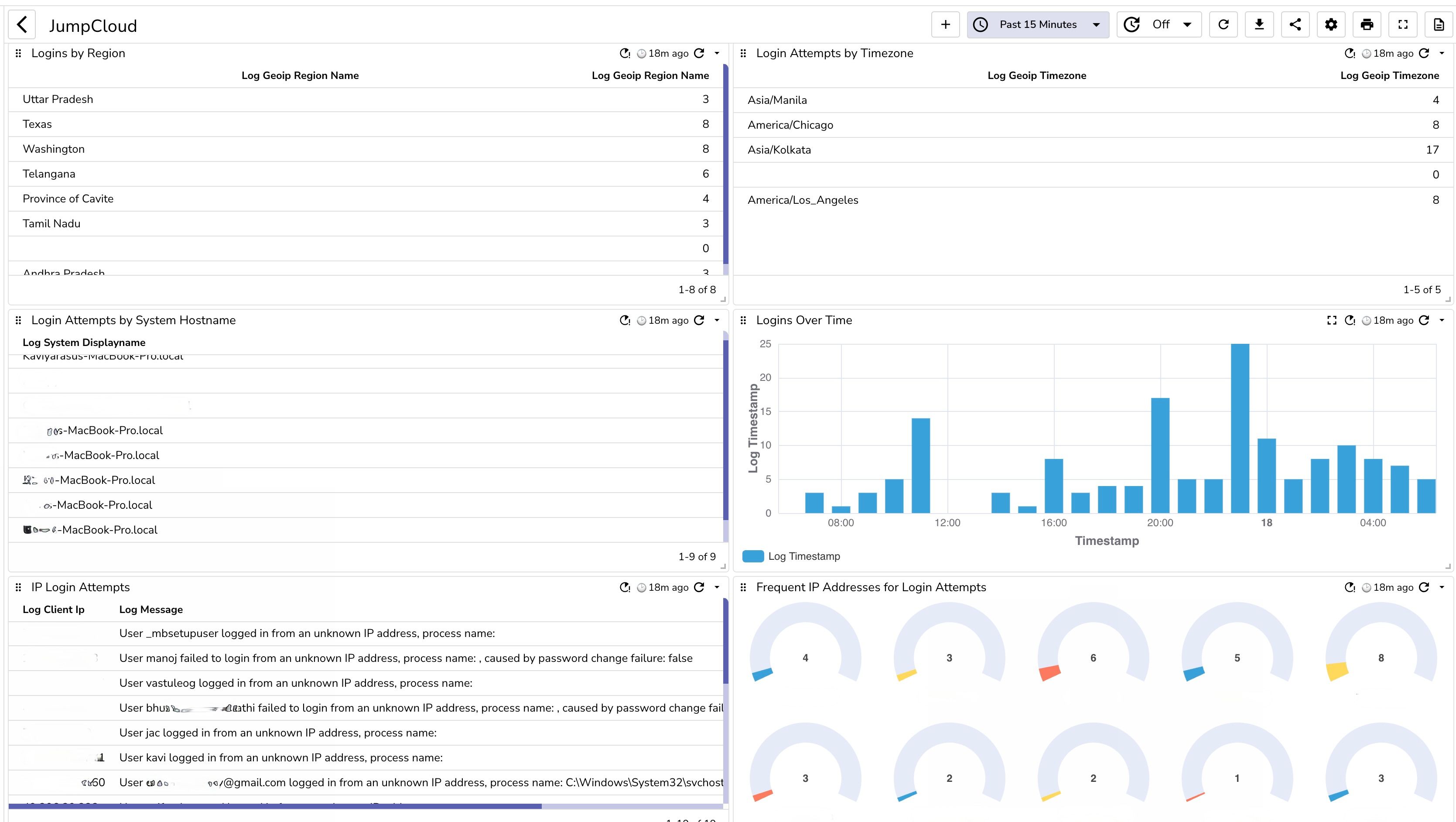
Integrating JumpCloud Insights with OpenObserve using AWS S3 and Lambda enables advanced security observability. The comparison below highlights the enhanced capabilities gained by sending JumpCloud logs to OpenObserve
| Feature/Aspect | JumpCloud Insights Alone | JumpCloud Insights Ingested into OpenObserve |
|---|---|---|
| Data Storage | AWS S3 (raw data) | AWS S3 with live ingestion in OpenObserve |
| Real-time Analytics | Limited | Full real-time visualization |
| Customized Dashboards | None | Available in OpenObserve |
| Security Monitoring | Basic | Enhanced with detailed metrics and logs |
| Setup Complexity | Moderate | Moderate, with Lambda and template.yaml |
| Scalability | Depends on S3 limitations | Scalable via OpenObserve |

Chaitanya Sistla is a Principal Solutions Architect with 17X certifications across Cloud, Data, DevOps, and Cybersecurity. Leveraging extensive startup experience and a focus on MLOps, Chaitanya excels at designing scalable, innovative solutions that drive operational excellence and business transformation.