Comprehensive Guide to AWS WAF: Logging, Monitoring, and Visualization


Try OpenObserve Cloud today for more efficient and performant observability.
Get Started For Free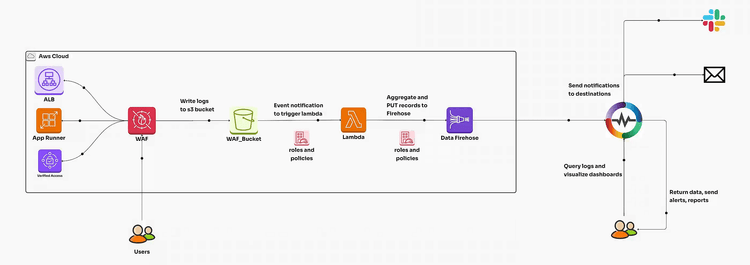
AWS Web Application Firewall (WAF) is a powerful tool designed to protect web applications from common exploits and vulnerabilities. By analyzing HTTP/S traffic, AWS WAF helps you mitigate threats such as SQL injection, cross-site scripting (XSS), and more, ensuring robust security for your applications. Whether you're securing an API Gateway, Amazon CloudFront, or an Application Load Balancer, AWS WAF provides a customizable and scalable solution.
For step-by-step instructions on setting up AWS WAF, refer to the AWS WAF Getting Started Guide.
Logging in AWS WAF provides visibility into allowed and blocked requests, helping you:
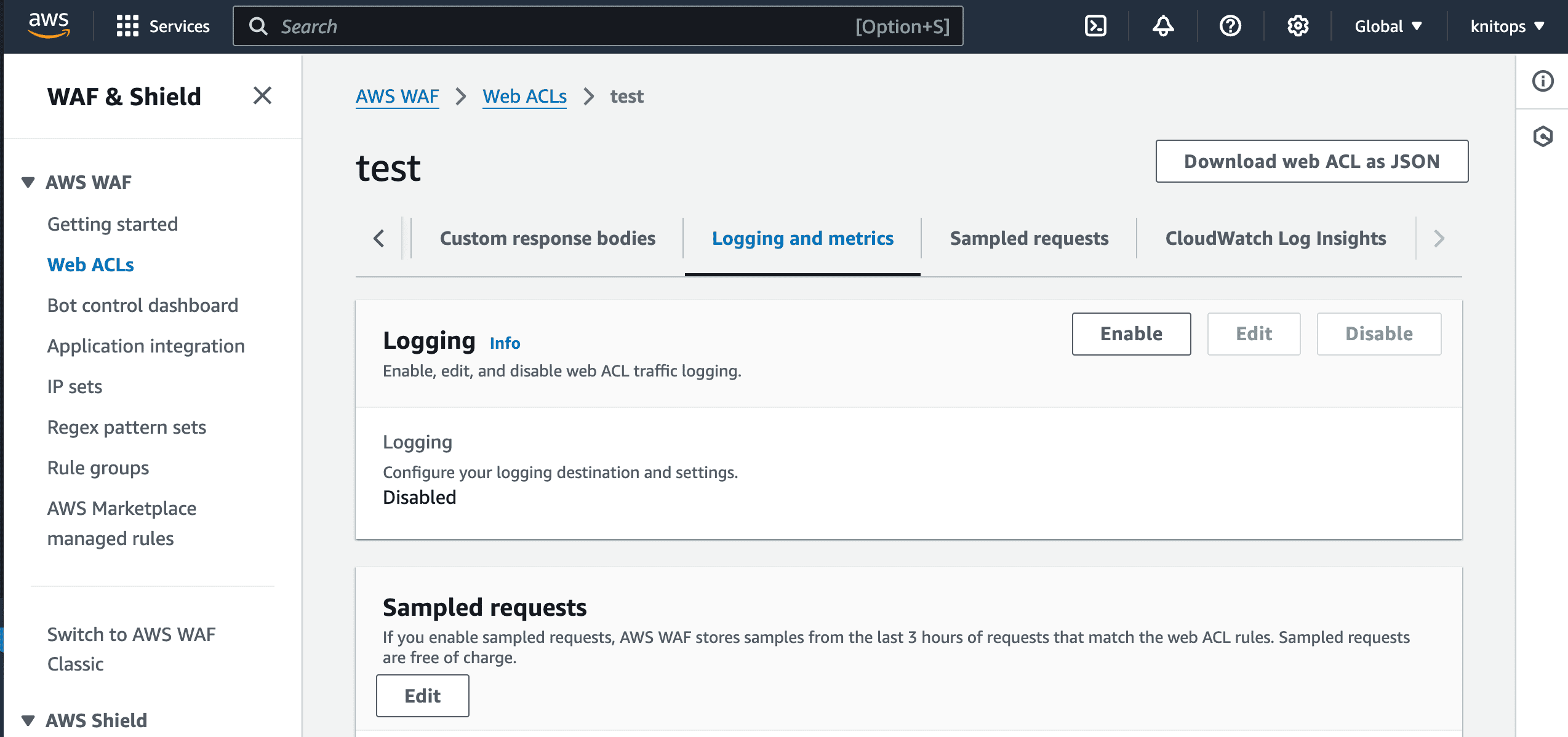
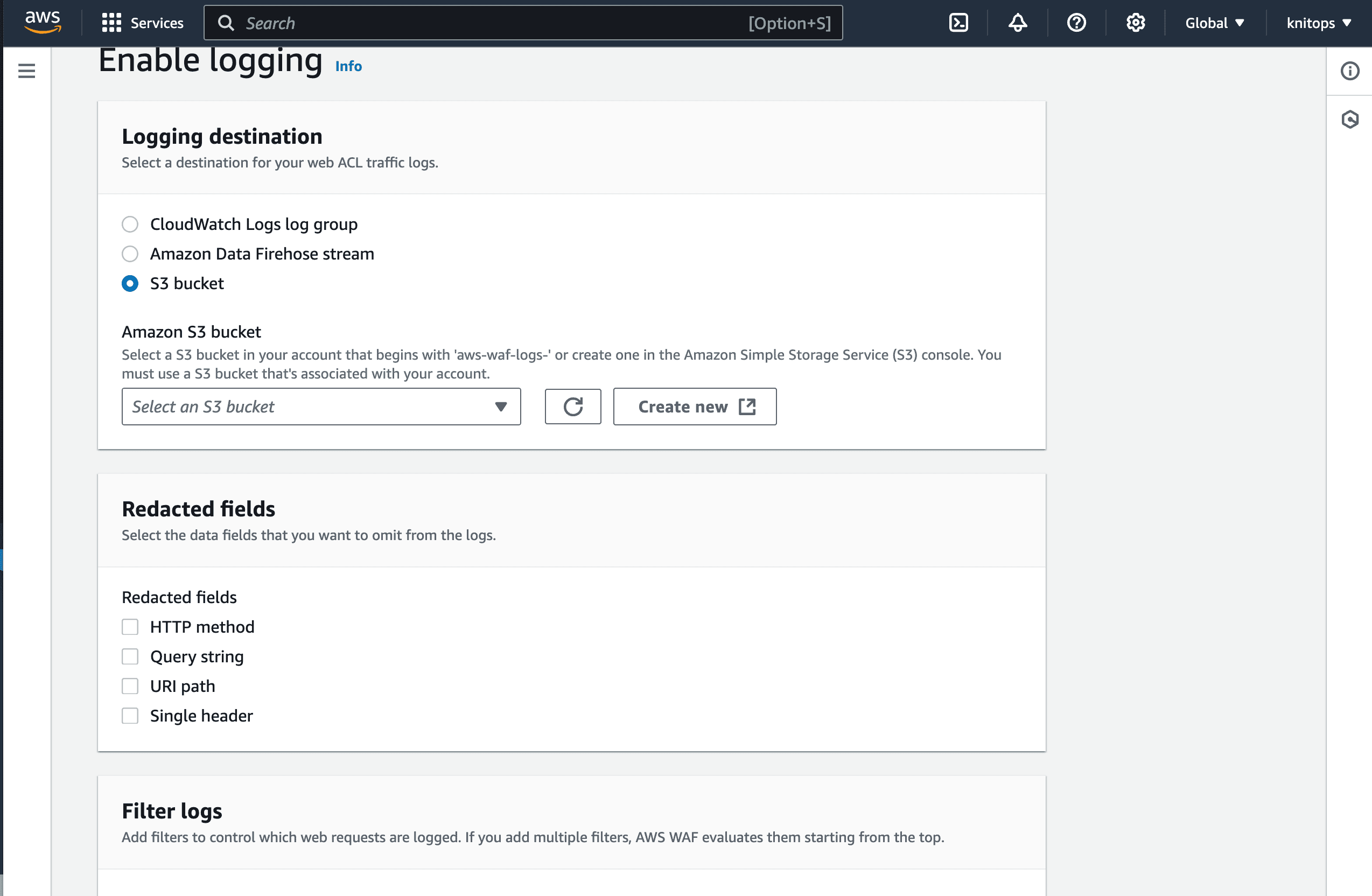
Use the CloudFormation template from our repository.
Upload the CloudFormation template to your AWS account.
Provide parameters such as:
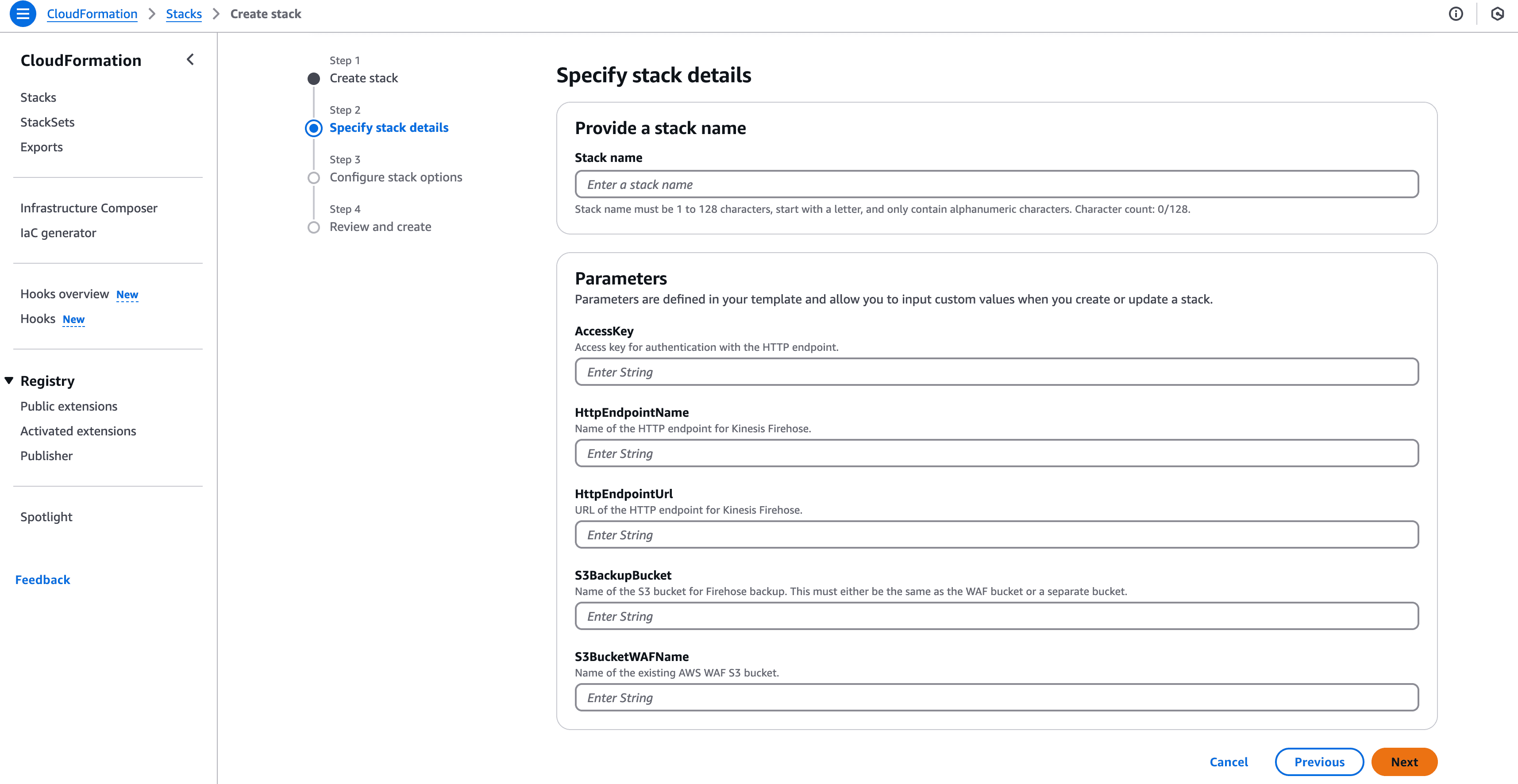
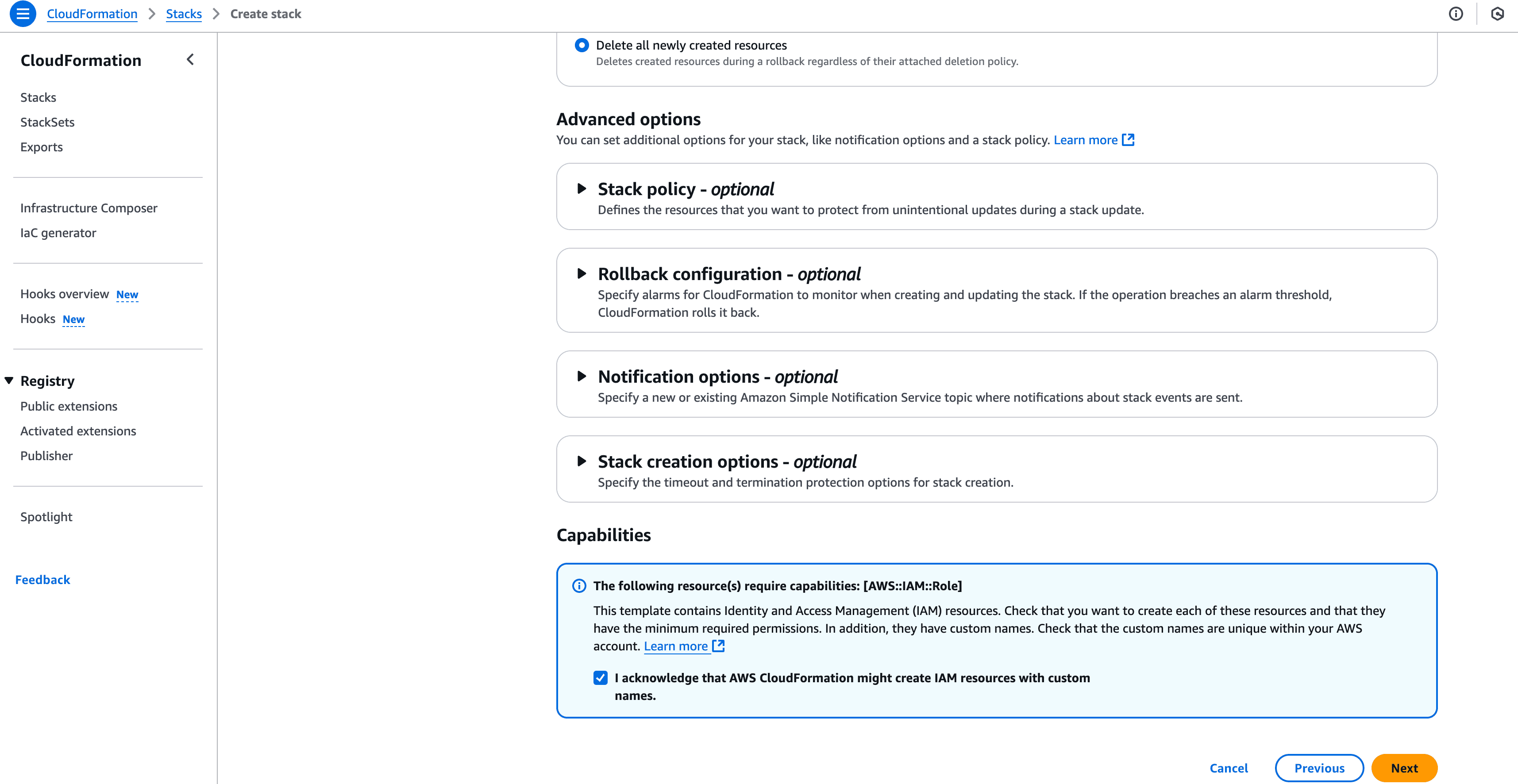
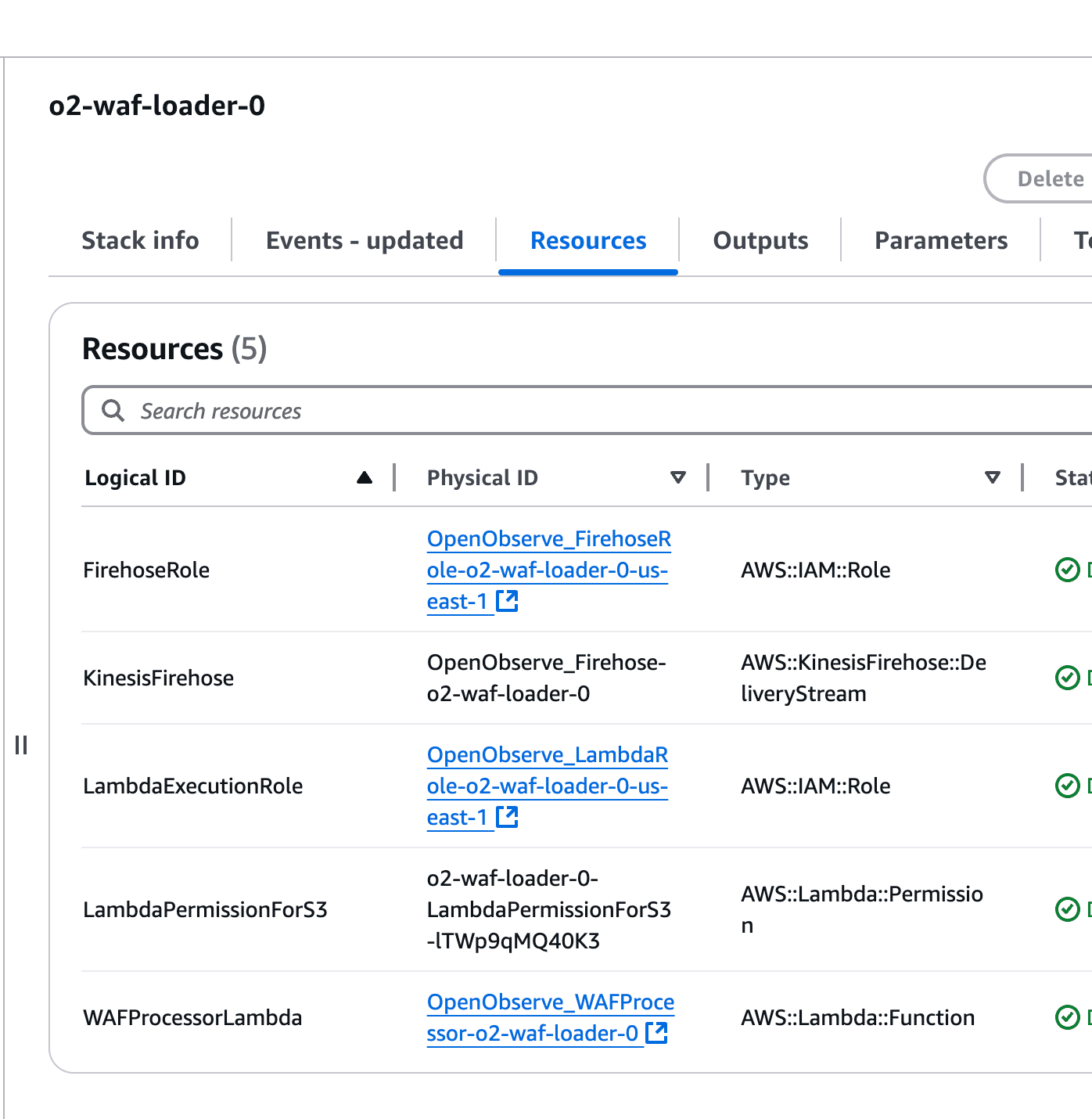
Ensure the IAM roles, Lambda function, Kinesis Firehose, and S3 configurations are created successfully.
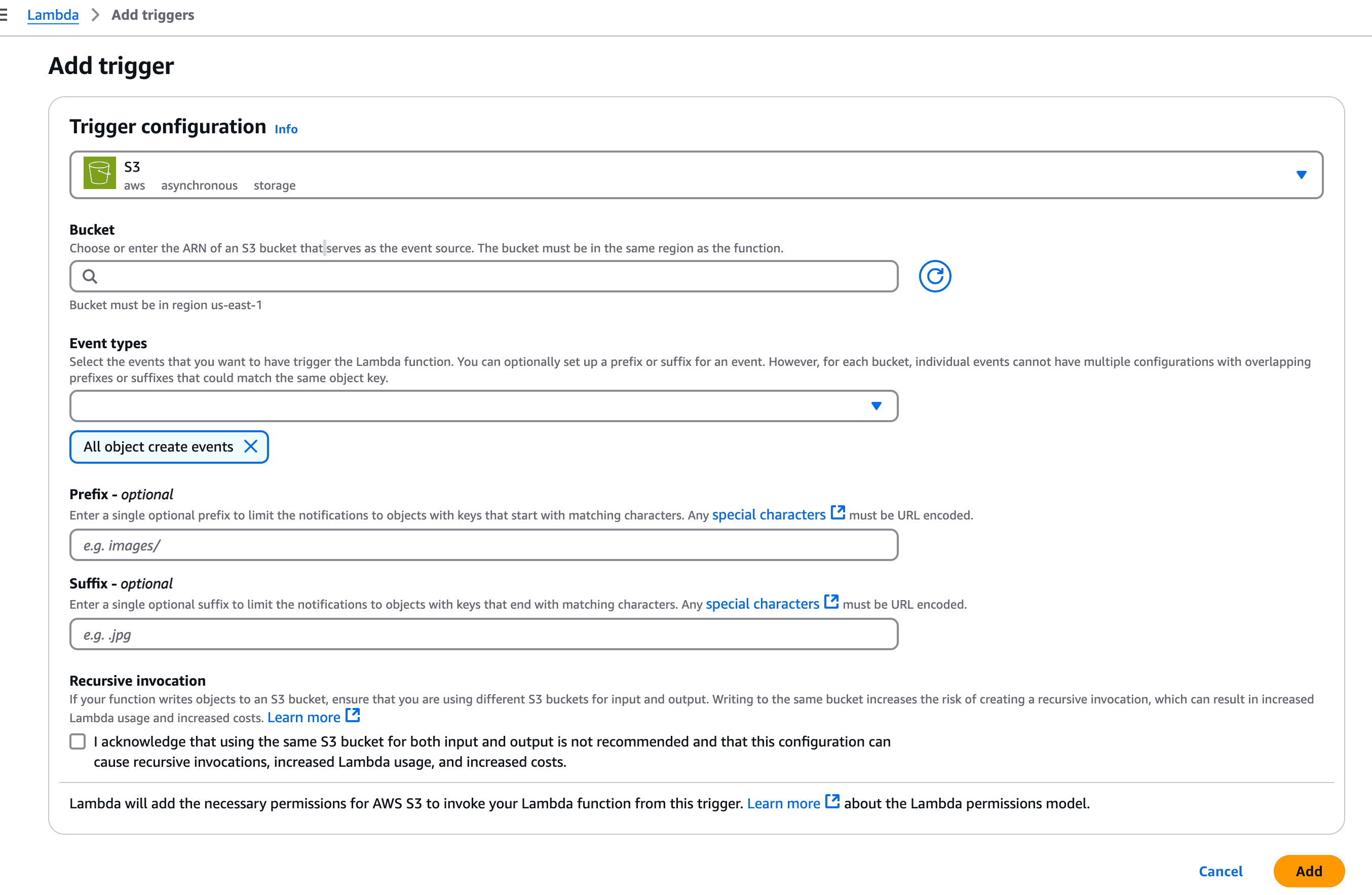
Cloudformation does not support enabling trigger on existing bucket so you will need to add the trigger manually as below.
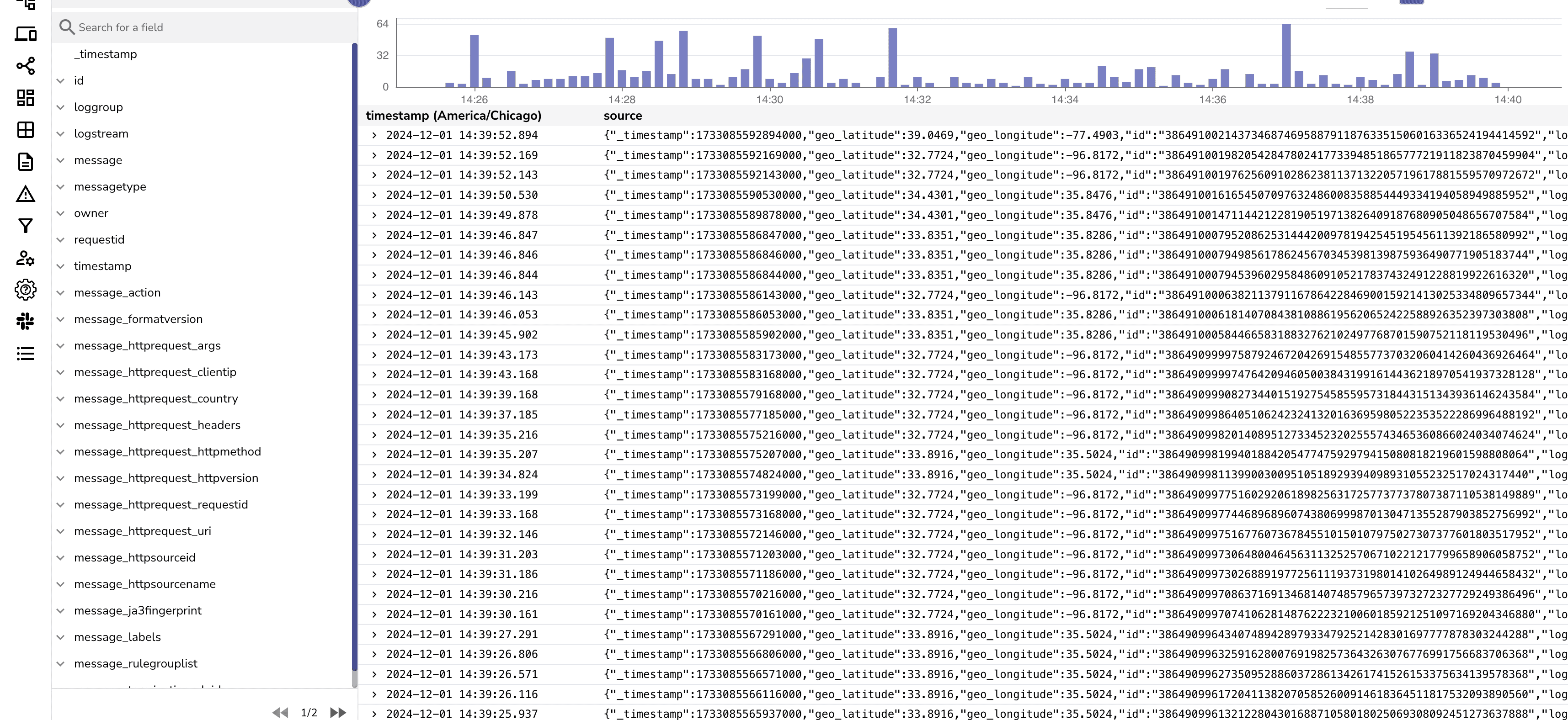
Go to your OpenObserve dashboard and verify the logs by searching your stream.
With OpenObserve, you can create custom dashboards to:
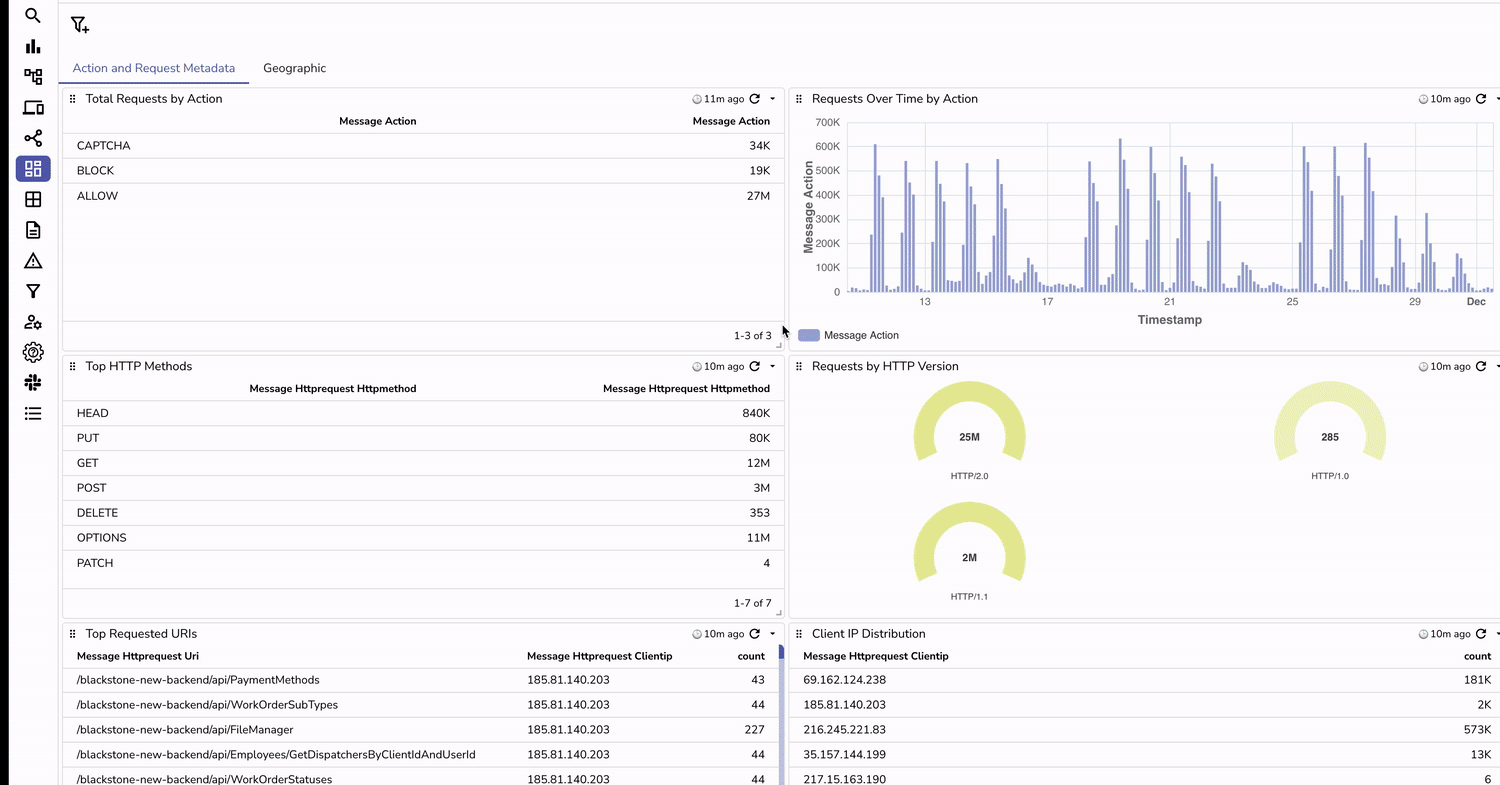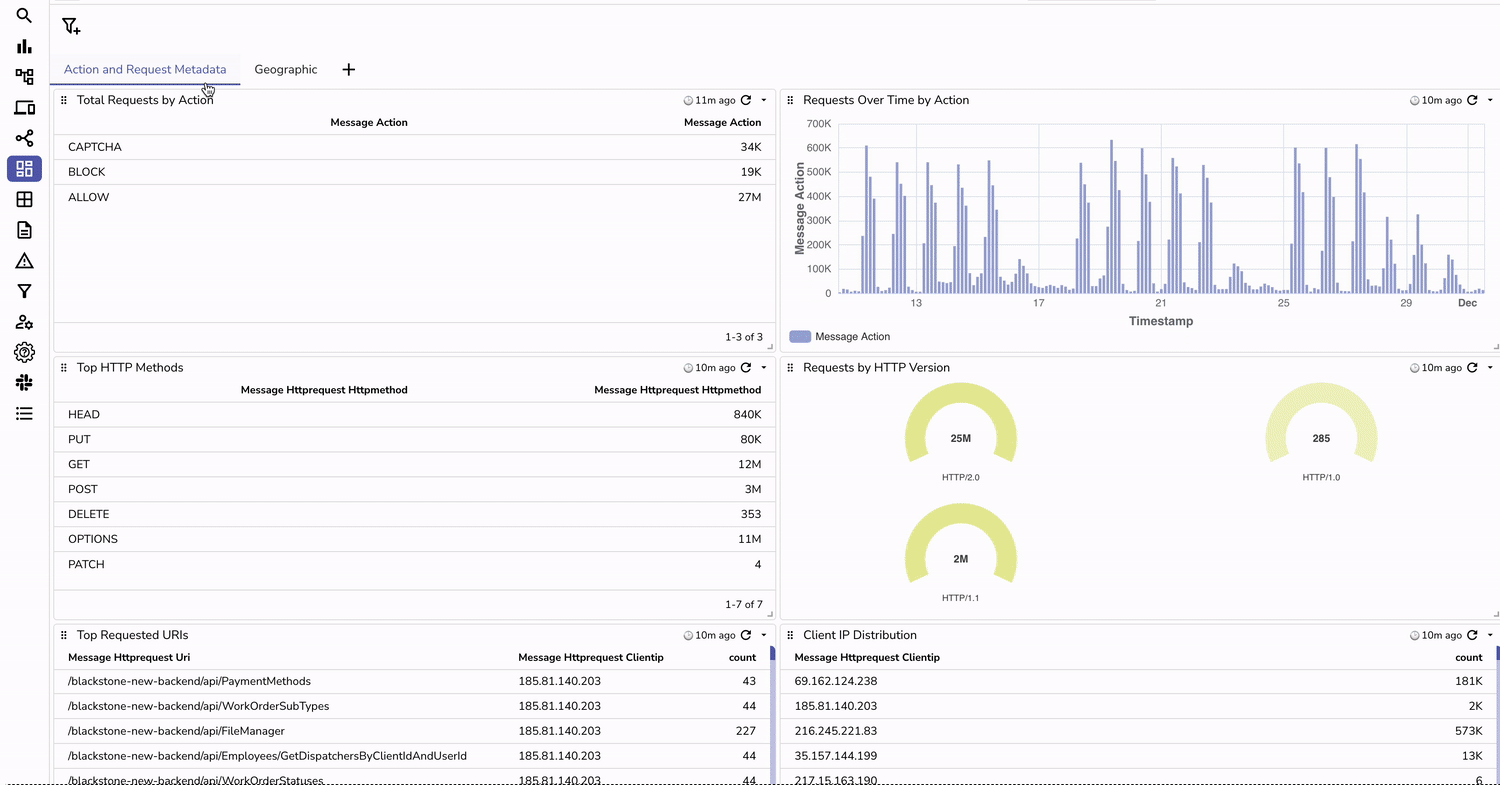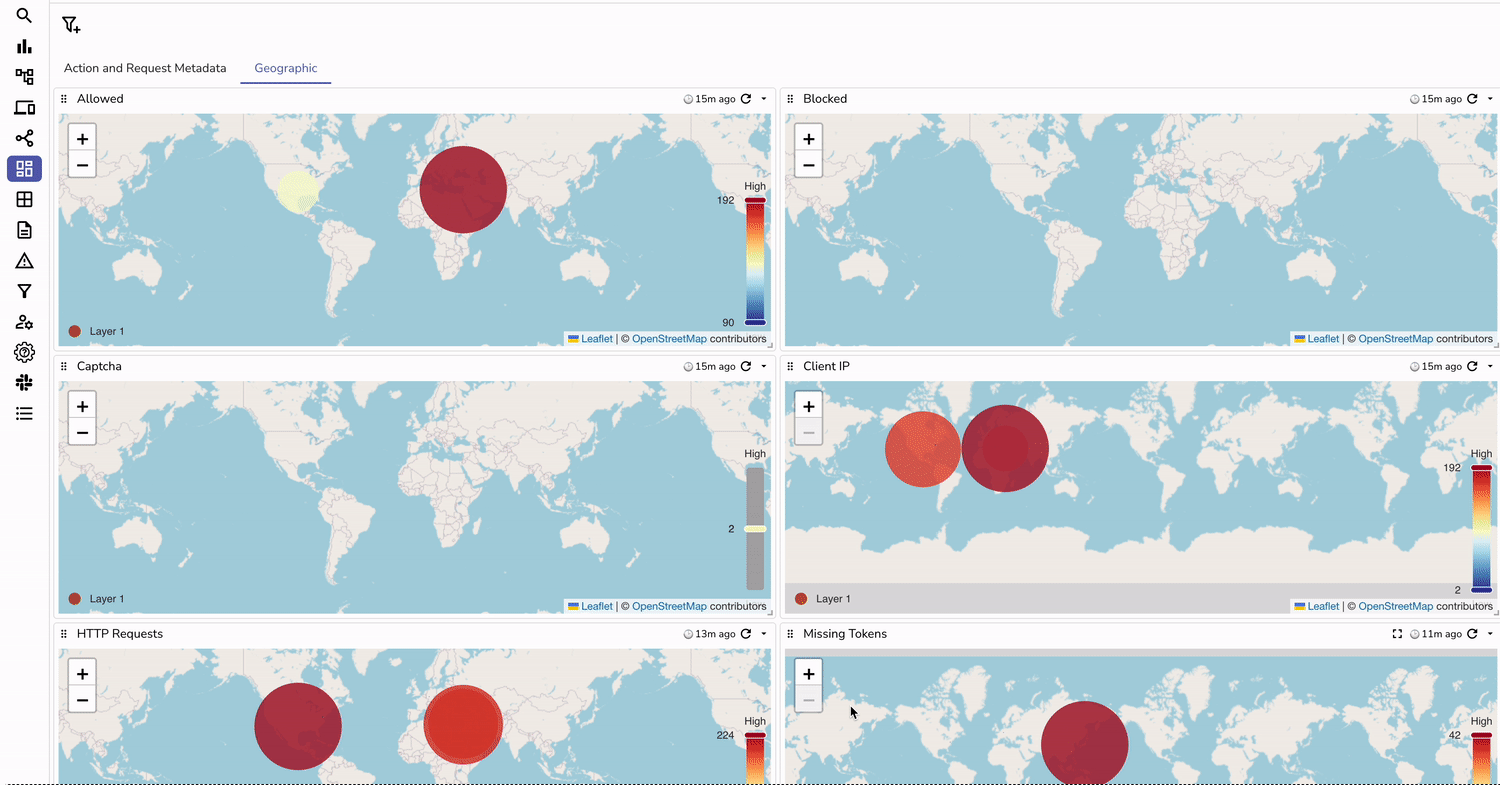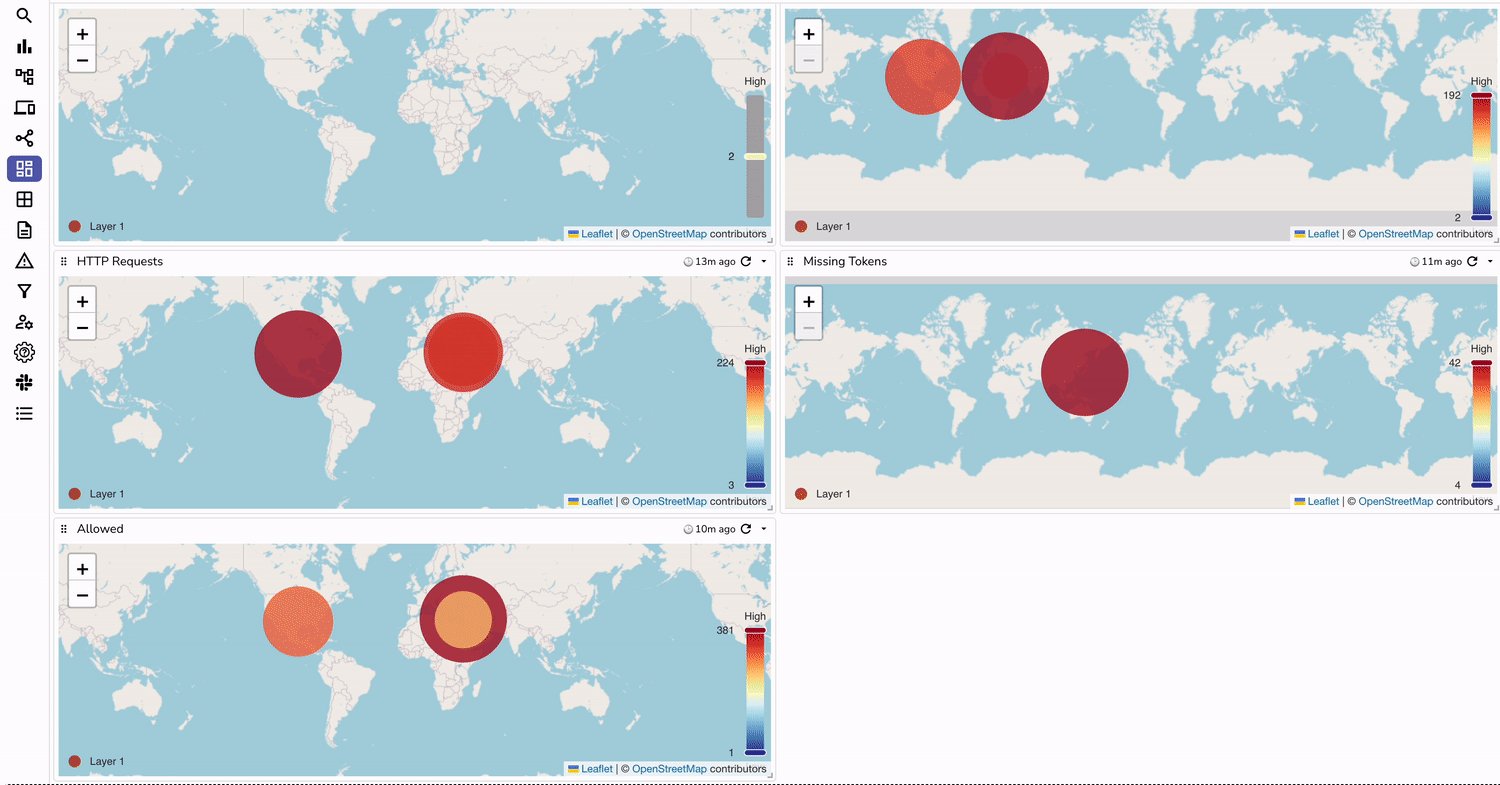
You can download our AWS WAF dashboard to get started with basic charts.
allow, deny, and challenge actions. 
The combination of AWS WAF logging and OpenObserve dashboards provides unparalleled insights into your web application’s security. From real-time monitoring to historical data analysis, these tools empower you to safeguard your infrastructure effectively. With intuitive dashboards, you can quickly identify malicious activity, optimize rules, and track API Gateway usage.
Detailed logs and visualizations ensure compliance and make troubleshooting seamless. Automated alerts and reports keep you informed about anomalies, while centralized monitoring offers a unified view of your application’s security posture. Together, AWS WAF and OpenObserve deliver a robust, scalable, and proactive solution to meet your web application security and monitoring needs.
| Feature | With OpenObserve | Without OpenObserve |
|---|---|---|
| Log Analysis | Interactive dashboards for deep insights | Limited to raw log files |
| Visualization | Real-time visual representation of traffic | Limited visualization |
| Threat Tracking | Identify patterns and malicious activity | Manual analysis required |
| Alerts | Custom alerts for anomalies or specific events | Limited alerting mechanism |
| Reports | Automated, scheduled reports with actionable insights | Requires manual reporting efforts |
| Centralized Monitoring | Single pane of glass for AWS WAF and other logs | Logs siloed, no unified view (imagine having org accounts) |
| Automation | Integrated alerts and workflows for quick responses | No automation capabilities |
Ready to get started with OpenObserve to ingest AWS WAF logs for detailed analysis? Visit our cloud version to quickly setup your OpenObserve account.

Chaitanya Sistla is a Principal Solutions Architect with 17X certifications across Cloud, Data, DevOps, and Cybersecurity. Leveraging extensive startup experience and a focus on MLOps, Chaitanya excels at designing scalable, innovative solutions that drive operational excellence and business transformation.